Benefits of using DNSSEC
Prevents Fake Websites: DNSSEC makes it much harder for attackers to poison the cache and redirect you to fake websites.
Protects Your Information: By reaching the real website, you're less likely to have your personal information stolen by imposters.
Safer Online Experience: DNSSEC helps to create a more secure online environment for everyone.
Brand protection: there's a marginal danger that a person who wants to reach your website with your domain, ends up in a fake website
Which attacks help DNSSEC mitigate ?
DNSSEC, or
Domain Name System Security Extensions, helps mitigate attacks that target vulnerabilities in the traditional DNS system, which wasn't designed with security in mind. Here are some common attacks that DNSSEC can help prevent:
- DNS Spoofing/Cache Poisoning: This attack involves injecting fake DNS data into a resolver's cache, causing it to direct users to malicious websites instead of the legitimate ones they intended to visit. DNSSEC uses digital signatures to verify the authenticity of DNS records, making it harder for attackers to tamper with them.
- DNS Hijacking: In this attack, attackers redirect DNS queries to a different name server, potentially leading users to a malicious site. DNSSEC helps ensure that users are directed to the correct name server by validating the source of the DNS information.
- Man-in-the-Middle Attacks: These attacks involve attackers intercepting communication between a user and a DNS server. DNSSEC encrypts communication between resolvers and validating servers, making it more difficult for attackers to eavesdrop and steal sensitive information.
What is the Chain of Trust ?
The chain of trust in DNSSEC is a critical concept for validating the authenticity of DNS records. It works like a series of verified handshakes throughout the DNS lookup process. Here's how it goes:
Digital Signatures: Imagine each DNS zone (like ".com" or "example.org") has a special key for signing DNS records. This key is split into two parts: a public key (DNSKEY record) and a private key (kept secret by the zone administrator). The public key is published in the zone itself, while the private key is used for signing.
Delegation Signer (DS) Records: Since DNS is hierarchical, a parent zone (like ".com") delegates authority for child zones (like "example.com") to their own name servers. To establish trust in this delegation, the parent zone includes a special record called a Delegation Signer (DS) record. This DS record contains a hash of the child zone's public key (DNSKEY). PDNS provides this for every domain that has been activated DNSSEC, so you can provide this information to the Registrar's Portal and effectively establish the Chain of Trust.
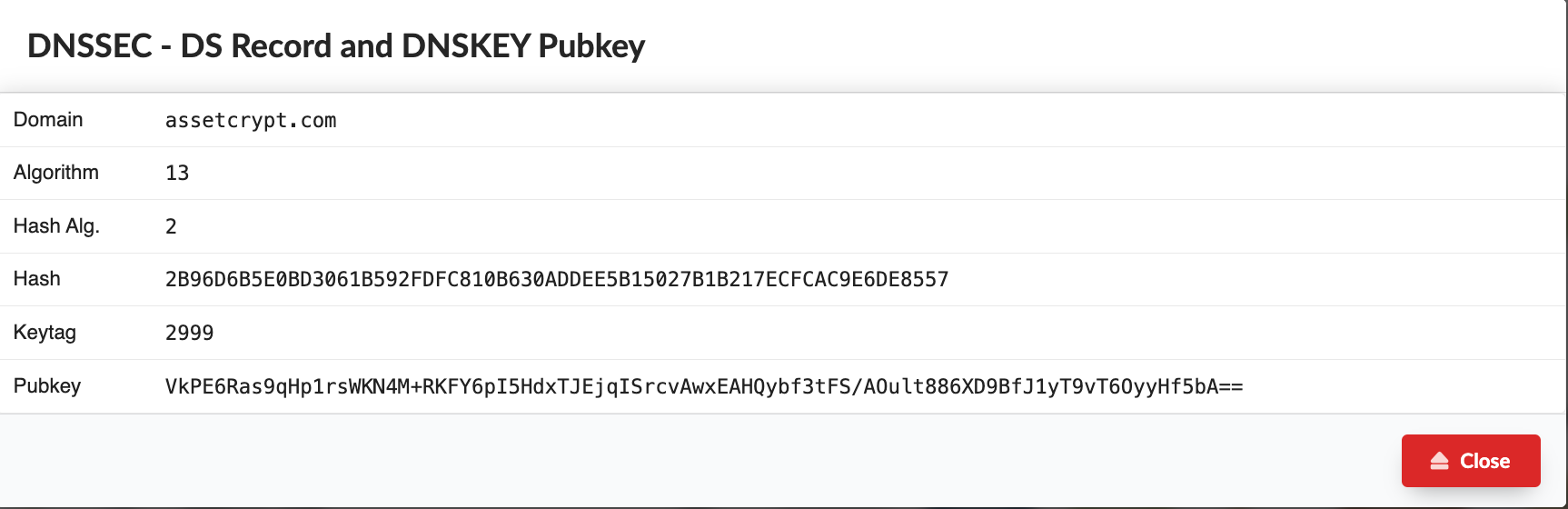 Validation Process
Validation Process: When your computer asks a DNS resolver for a website address, the resolver follows the DNS hierarchy. As it reaches each zone, it checks the DS record in the parent zone. It then hashes the child zone's public key it receives and compares it to the hash stored in the DS record. If they match, the resolver can trust the public key and the signed records in the child zone.
This process continues up the chain of zones until it reaches the root zone, which has a pre-configured trust anchor. Since there's no parent zone for the root, these root keys are explicitly trusted by DNSSEC-enabled resolvers.
Think of the chain of trust like a chain reaction where each validated key vouches for the authenticity of the next zone in the hierarchy. This ensures that you ultimately get the correct DNS information from the legitimate source, reducing the risk of tampering or malicious redirection.
DANE Protocol for E-mail Security
DANE, which stands for
DNS-based Authentication of Named Entities, works with DNSSEC (Domain Name System Security Extensions) to significantly improve email security. Here's what DANE offers:
Reliable Encrypted Email Delivery: Unlike the traditional method (STARTTLS) where encryption can be negotiated after connection, DANE ensures email servers establish encrypted TLS connections from the start. This eliminates the possibility of attackers
downgrading the connection to unencrypted mode and intercepting emails.
Prevents Man-in-the-Middle Attacks: DANE relies on TLSA records (TLS Authentication records) published in a domain's DNS. These records specify the valid TLS certificate for the mail server. When sending an email, the sending server checks the recipient domain's TLSA record and verifies the receiving server's certificate against it. This ensures communication with the legitimate server and prevents attackers from impersonating it with a fake certificate.
Improved Trust and Authentication: By verifying certificates, DANE ensures email servers are talking to the intended recipient. This reduces the risk of emails being delivered to malicious servers that could steal information or spread spam.
Incremental Deployment: A major benefit is that DANE allows for a gradual rollout. Even if not all email servers support DANE, those that do can still benefit from the increased security. Traditional servers can still function using opportunistic TLS.
You can read more about DANE in this
article.


